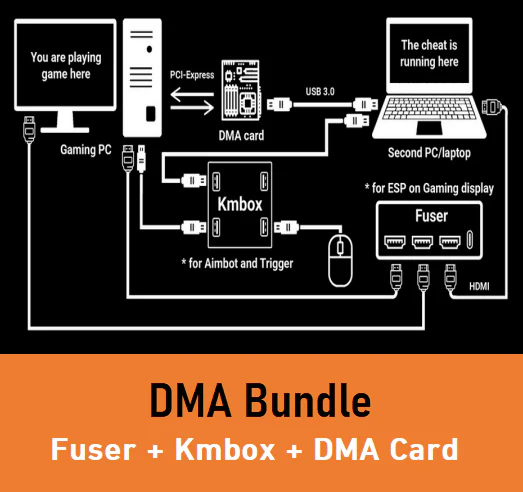
DMA Hack or Direct Memory Access Hack is a type of attack that relies on direct access to the computer or system’s memory without going through the Central Processing Unit (CPU). The main goal of this type of attack is to extract data or manipulate operations occurring in memory.
Definition of DMA:
DMA, or Direct Memory Access, is a technology used in computer systems that allows peripheral devices like network cards or storage units to access the main memory directly without the CPU’s intervention for each data transfer operation. This enables faster data transfer and reduces the load on the processor.
How does DMA Hack work?
In these types of attacks, the attacker exploits the ability of connected devices to access system memory directly using DMA technology. The attack can be carried out in various ways, including:
- Connecting a device with a DMA-supporting port: Devices supporting protocols like Thunderbolt or PCIe are examples of devices that provide DMA. If an attacker has physical access to your device and connects a compromised device such as a fake storage drive or advanced USB device, they can execute the attack by accessing the memory directly.
- Manipulating system memory: Once the attacker gains access to system memory via DMA, they can read sensitive data like passwords, encryption keys, and other important information stored in memory.
- Injecting malicious code into memory: Using DMA, an attacker can inject harmful code into the memory of active software or systems, potentially taking control of ongoing processes.
- Stealth: These types of attacks are difficult to detect because memory access occurs outside the supervision of the operating system and antivirus software.
See also: Fuser
Table of Contents
ToggleRequirements for the Attack:
- Physical access: In most cases, the attack requires physical access to the device. For example, the attacker might insert a device capable of executing DMA into a PCIe or Thunderbolt port of the targeted computer.
- DMA-supporting devices: Devices that support DMA technology, like laptops with Thunderbolt or USB-C ports and servers with PCIe slots, are often exploited.
Famous DMA Attacks:
- Thunderclap Attack (2019): This attack exploited Thunderbolt technology to execute DMA through an externally connected device. Attackers bypassed security protections and accessed memory.
- PCILeech: A software tool developed to execute DMA attacks using external PCIe devices. The attacker could read and write system memory directly.
Protection from DMA Attacks:
- Disabling DMA ports when not in use: Users or administrators can disable or restrict the use of Thunderbolt and PCIe ports, especially in sensitive environments.
- Memory Encryption: Security solutions using memory encryption can reduce the risk of sensitive data being compromised.
- Using Secure Devices: Device manufacturers like Apple and Microsoft have started implementing technologies to protect devices from DMA attacks, such as DMA guard during sleep mode.
- Security Updates: Users should ensure their devices have the latest security updates to avoid vulnerabilities that could be exploited via DMA.
How Traditional Protection Techniques are Bypassed:
- Bypassing the Operating System:
One reason why DMA attacks are effective is that attackers bypass the operating system entirely. Traditional security techniques like antivirus and firewalls rely on monitoring software behavior and interactions with the OS, but DMA attacks occur outside the OS’s oversight, making them invisible to these tools. - Using External Devices:
Attacks often rely on connecting an external device with DMA capabilities, such as hacked USB, PCIe, or Thunderbolt devices. Attackers may design devices that appear legitimate but contain built-in equipment to read and write memory data. These devices can be well-hidden to seem harmless. - Remote Attacks:
Although most DMA attacks require physical access, some techniques may enable remote attacks. For instance, if a device has a Thunderbolt port and the attacker can access the network, they might be able to execute the attack by connecting to the device via a DMA-enabled interface. - Attacks on Virtual Machines (VMs):
Virtual machine environments rely on resource sharing between virtual hosts, and DMA attacks could be used to target virtual systems by accessing shared memory between hosts.
Tools Used in DMA Attacks:
- PCILeech:
A well-known tool for executing DMA attacks. It works by connecting a PCIe device to the computer. PCILeech can read and write to system memory directly, allowing for data theft or malware injection. - Inception:
A DMA attack tool used to bypass security on computers by accessing physical memory. It allows attackers to decrypt passwords and bypass login screens. - Thunderbolt Exploits:
Thunderbolt exploits are some of the most famous examples of DMA-based attacks. Devices with Thunderbolt support have direct memory access capabilities, and if these capabilities are exploited, attackers can access sensitive data in the system.
Additional Protection Measures from DMA Attacks:
- Relying on “IOMMU” (Input-Output Memory Management Unit):
IOMMU units are used to restrict devices’ ability to access system memory directly. This technology segments memory and designates specific regions that external devices can access. Many modern systems rely on IOMMU as a defense against DMA attacks. - Enabling Physical Security:
In sensitive work environments, physical measures can be taken to protect against DMA attacks. For example, not leaving devices unattended and using physical locks on ports (like Thunderbolt or USB) to prevent unauthorized devices from accessing these ports. - Using Secure Boot:
Some systems rely on secure boot technology to ensure that the device has not been tampered with before the OS boots up. This prevents malicious software that may attempt to control the system via DMA at boot time. - Implementing Device Control Policies:
This involves controlling which devices are allowed to communicate with the computer via ports like Thunderbolt and PCIe. Companies can adopt device management technologies to prevent unauthorized devices from accessing the system.
See also: KMBox
The Future of DMA Attacks:
With the increasing reliance on technologies like Thunderbolt and PCIe, DMA attacks are likely to remain a significant threat, especially in environments that require high-speed data transfers. Therefore, it’s crucial to improve protection technologies and ensure that devices support modern security mechanisms.
DMA attacks present a complex threat as they rely on manipulating the system’s physical memory through peripheral devices. Despite advances in security methods such as IOMMU and Secure Boot, there remains a significant challenge in preventing attacks that rely on physical access to the device.